AI Commits Fraudulent Activity
 |
| Source - Future of Dental Office with Blended Reception |
Watch out for Scammers!
 |
| Source - Lewis & Clark County |
Hey guys, this week I have been applying my digital literacy skills to explore the risks individuals face using the internet.
During my research, I discovered one of the greatest risks on the internet in 2024 was the threat of malicious activity from AI.
These shocking acts may be performed through Phishing and Criminal Computer Software which scammers use to create compelling fraudulent schemes.
What is AI?
Artificial Intelligence (AI) is a cutting-edge technology that has rapidly spread worldwide since its breakthrough. This advanced technology enables computers to mimic human-like thinking and actions in myriad applications. Examples of AI include digital assistants such as Alexa and Siri, which have voice interactive abilities.
 |
| Was John Connor right?? |
Phishing
Phishing occurs when scammers and cybercriminals try to impersonate somebody they are not. These are mainly large companies that an individual will have a relationship with. For example, Banks and Phone service companies. They do this hoping that once they have gained the victim's trust, they will succeed in asking for money or passwords relevant to their cause of contact. They are very believable when they use AI to assist in the crime. AI can create fake, realistic social media or company accounts where they will send texts and emails using appropriate language masking themselves like a wolf in sheep's clothing.
Bank, S. (n.d.). How Scammers Are Using AI. Www.seacoastbank.com. https://www.seacoastbank.com/resource-center/blog/ai-a-new-tool-for-scammers
 |
| Google Image Clipart |
Criminal Computer Software (Malware)
Cybercriminals use methods like Malware to steal but not crack passwords or security keycodes. Similar to phishing they trick their users into thinking they are legitimate and trustworthy to obtain their information.
Two types of malware include:
KEYLOGGERS - Programs that monitor all user activities on the device, gaining access to passwords and compromising privacy.
SCREENSCRAPERS - Image-capturing technology installed on your device to capture saved password suggestions and private information such as bank details.
Gillis, A. (2021, May). What Is Password Cracking? SearchSecurity. https://www.techtarget.com/searchsecurity/definition/password-cracker
Why is this important?
Malware and Phishing are the leading cybersecurity threats related to data theft, system corruption, privacy exploitation, blackmail, and financial losses.
These threats are relevant today, spreading across all frames of networks exploiting individuals into revealing sensitive information or installing malicious programs. Business, Education, Government & Healthcare institutions as well as individuals are all common victims, these cybercriminals are persistent, and their prevalence is due to the technological age we live in.
Bank, S. (n.d.). How Scammers Are Using AI. Www.seacoastbank.com. https://www.seacoastbank.com/resource-center/blog/ai-a-new-tool-for-scammers
What you can do! 👇
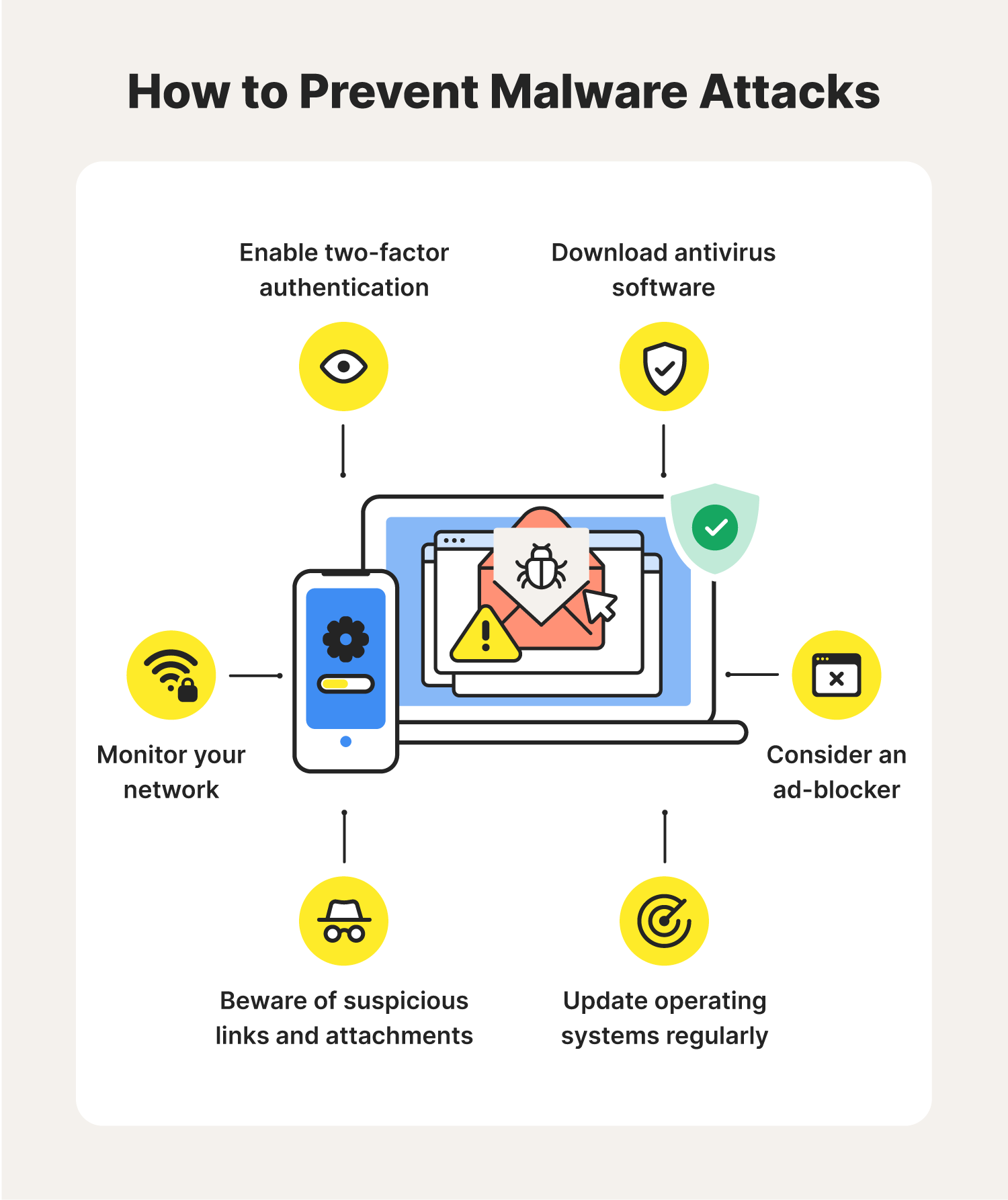 |
| Source - Malware Threats Norton |
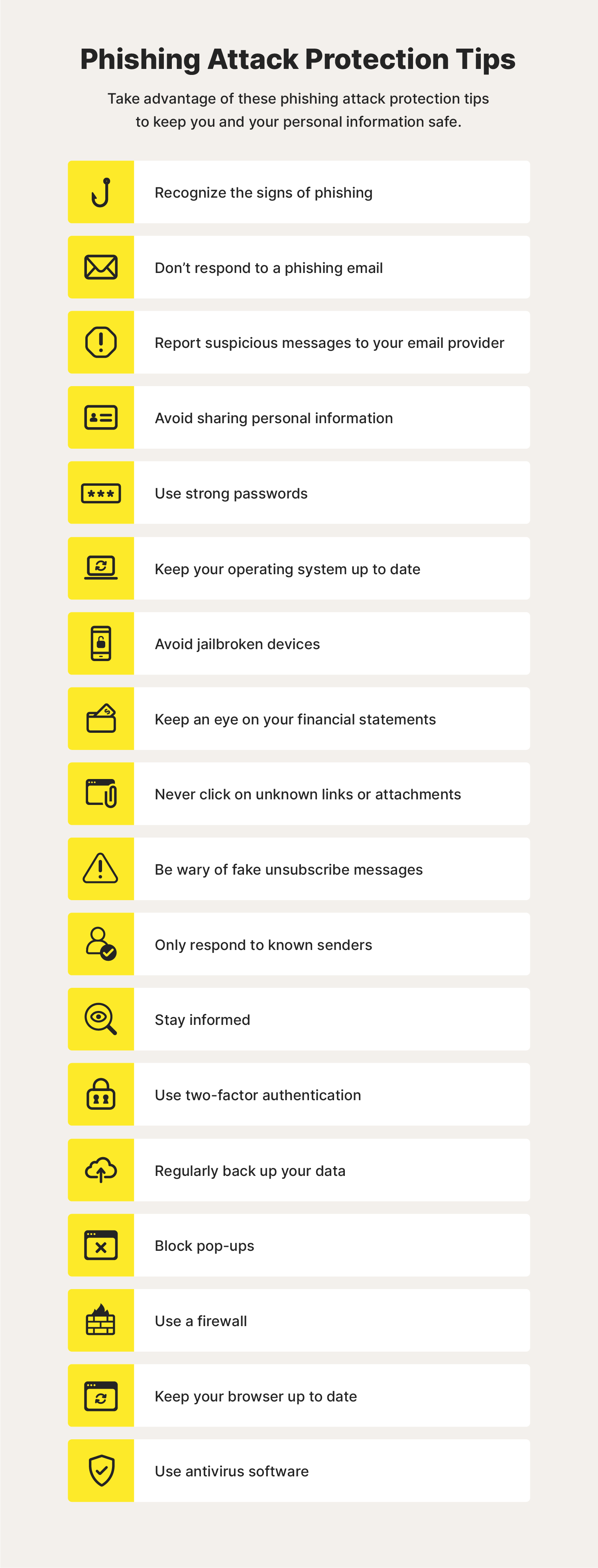 |
| Source - Phishing Protection Norton |
Below You Will Find A Clip Where I Critically Evaluated An Article on the Fraduelnt Activity that AI Commits Using The CRAAP Method.
Article - Unusual CEO Fraud via Deepfake Audio Steals US$243,000 From UK Company - Security News. (n.d.). Www.trendmicro.com. https://www.trendmicro.com/vinfo/au/security/news/cyber-attacks/unusual-ceo-fraud-via-deepfake-audio-steals-us-243-000-from-u-k-company
Video:
CRAAP is the method I used when critically evaluating the article. The process identified the credibility and relevancy of the report by simply scanning for information. This made it easy to evaluate my source and determine whether it applied to my research.








Comments
Post a Comment